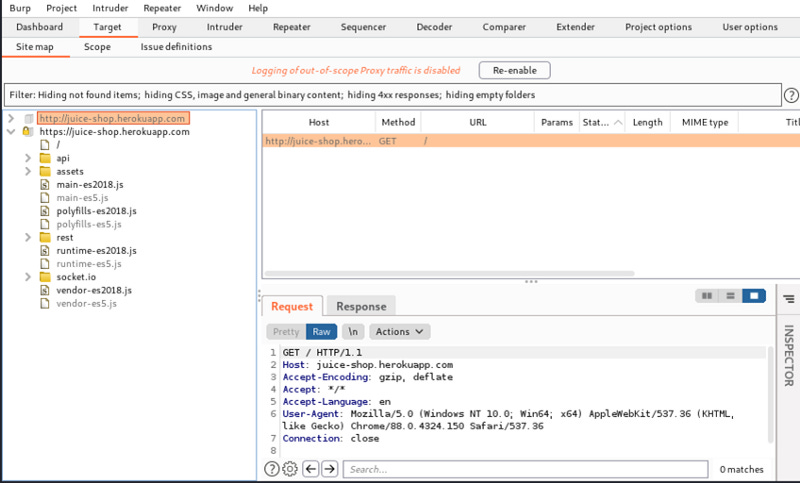
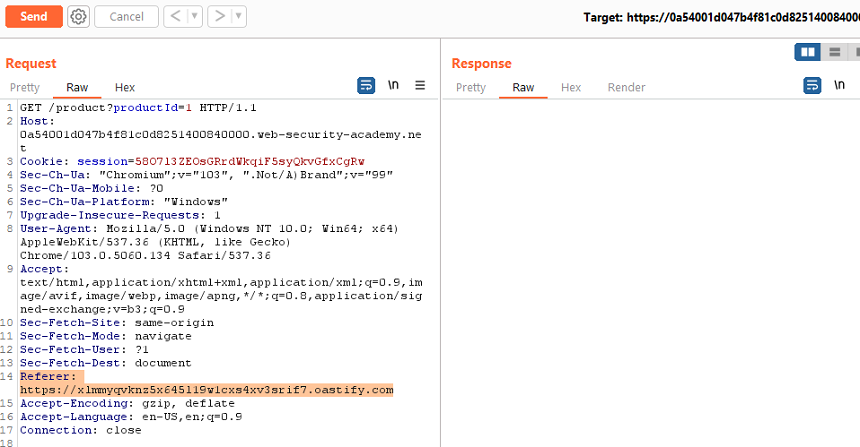
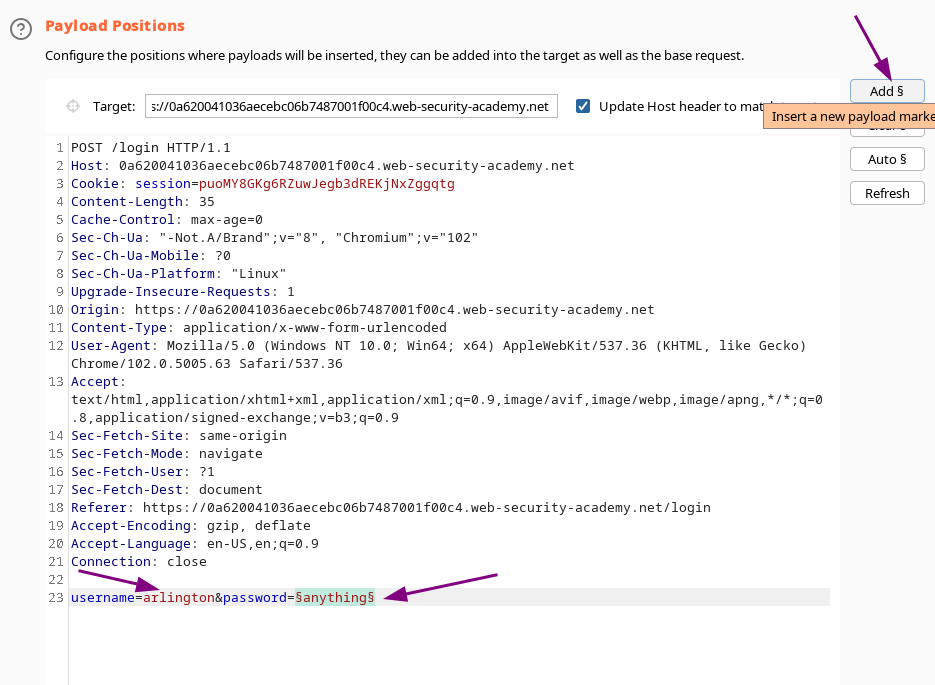
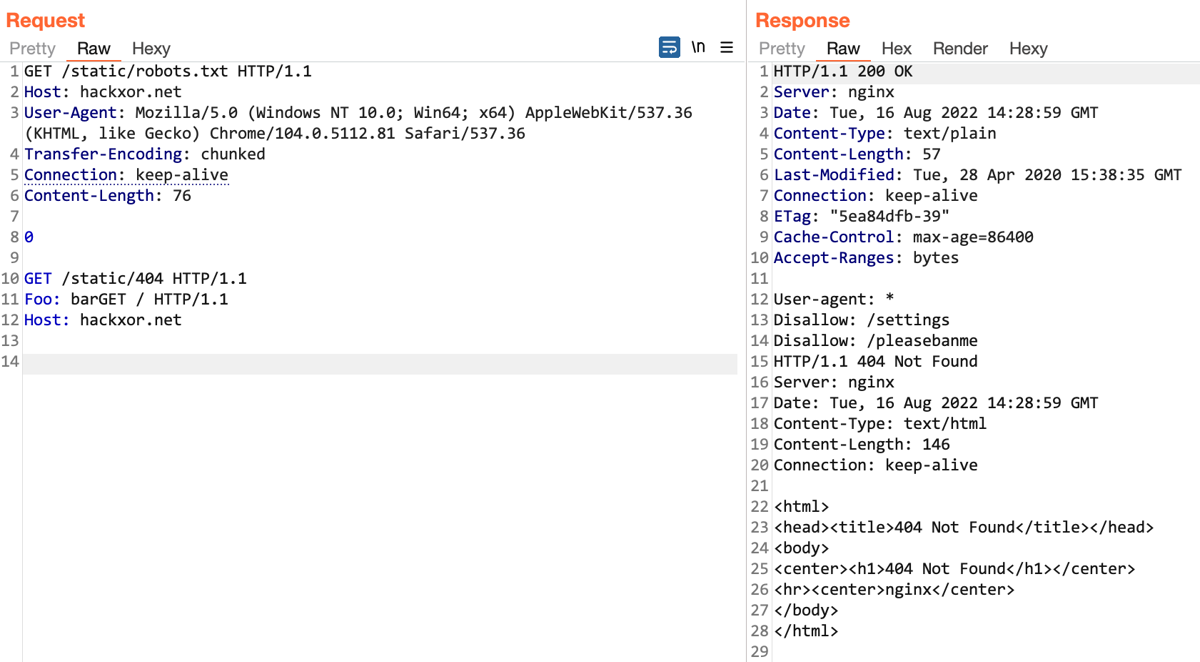
Generating CRSF POC using Brupsuite Figure 5 shows the screenshot of... | Download Scientific Diagram
How i exploit out-of-band resource load (HTTP) using burp suite extension plugin (taborator) | by MRunal | Medium
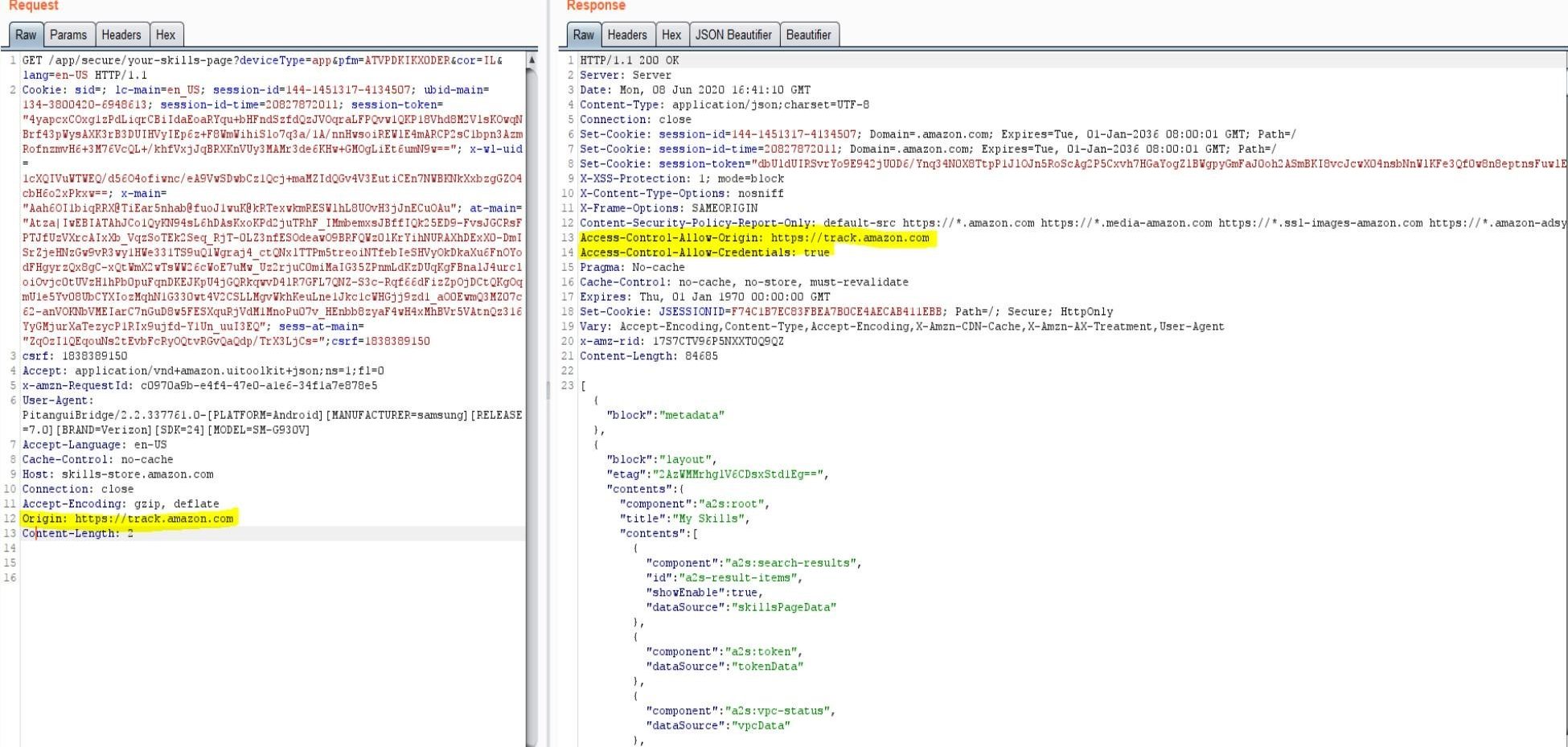
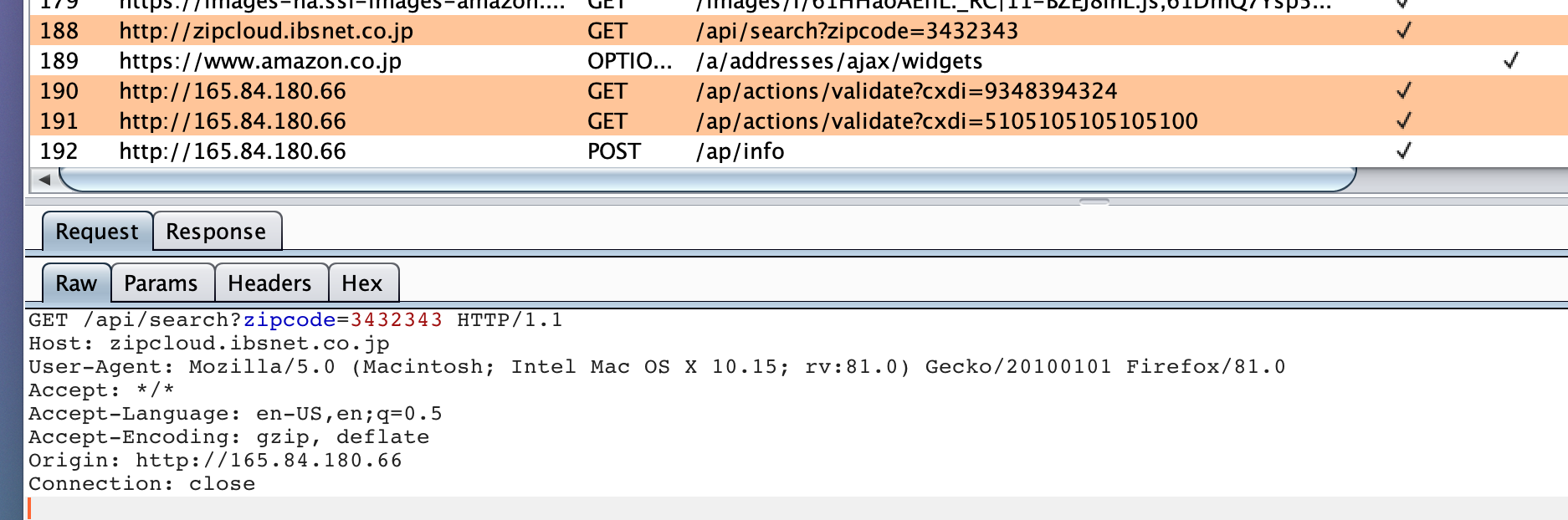
Keeping the gate locked on your IoT devices: Vulnerabilities found on Amazon's Alexa - Check Point Research

Amazon.com: A Complete Guide to Burp Suite: Learn to Detect Application Vulnerabilities: 9781484264010: Rahalkar, Sagar: Books